What is the CySA+ CS0-003 Exam Dumps?
The CompTIA CySA+ CS0-003 Exam Dumps validates a cybersecurity analyst's skills and knowledge in detecting, analyzing, and responding to cyber threats. It covers various security concepts, including security monitoring, incident response, threat intelligence, and vulnerability management.
Earning the CySA+ certification demonstrates your expertise in implementing and maintaining effective cybersecurity measures. It is an ideal credential for professionals seeking to advance their careers in cybersecurity or gain a competitive edge in the industry. Bypassing the CS0-003 exam, you will validate your understanding of the latest cybersecurity trends and best practices.
Key Features of the CS0-003 Exam
The CompTIA CySA+ (CS0-003) exam is a challenging but achievable assessment of your cybersecurity skills and knowledge.
Here are some key features of the exam:
- Format: The exam consists of 100 multiple-choice and performance-based questions.
- Time limit: You have 165 minutes to complete the exam.
- Passing score: You need to score 750 or higher on a scale of 1000 to pass the exam.
- Topics covered: The exam covers a wide range of cybersecurity topics, including security monitoring, incident response, threat intelligence, and vulnerability management.
- Prerequisites: CompTIA recommends that you have at least two years of hands-on experience in cybersecurity before taking the CySA+ exam.
To prepare for the CS0-003 exam, you can use a variety of resources, including the CompTIA study guide, online courses, and practice exams. With proper preparation, you can increase your chances of passing the exam and earning your CySA+ certification.
The CySA+ certification is a valuable asset for cybersecurity professionals. It demonstrates your expertise in implementing and maintaining effective cybersecurity measures. By passing the CS0-003 exam, you will validate your skills and knowledge and gain a competitive edge in the industry.
Why are CS0-003 Exam Dumps Useful?
CompTIA CySA+ (CS0-003) exam dumps are a valuable resource for preparing for the CySA+ certification exam. They provide a comprehensive overview of the exam objectives and can help you identify areas where you need additional study.
Here are some of the benefits of using CS0-003 exam dumps:
Identify your strengths and weaknesses: Exam dumps can help you identify areas where you are strong and where you need to improve your knowledge. This allows you to focus your studies on the areas that need the most attention.
Get a feel for the exam format: Exam dumps can help you get a feel for the format of the CySA+ exam. This can help you to avoid surprises on exam day and to manage your time effectively.
Practice answering exam questions: Exam dumps provide you with an opportunity to practice answering exam questions. This can help you to improve your test-taking skills and to increase your confidence on exam day.
It is important to note that exam dumps are not a substitute for studying the CompTIA CySA+ study materials. However, they can be a valuable supplement to your studies and can help you to increase your chances of passing the exam.
When using exam dumps, it is important to use them wisely. Do not simply memorize the answers to the questions. Instead, use them to identify areas where you need to improve your knowledge and to practice answering exam questions.
CySA+ CS0-003 Objectives Overview
The CompTIA CySA+ (CS0-003) certification exam covers a wide range of cybersecurity topics, including security monitoring, incident response, threat intelligence, and vulnerability management.
The exam objectives are divided into six domains:
- Security Monitoring and Analysis
- Incident Response
- Threat Intelligence
- Vulnerability Management
- Identity and Access Management
- Security Assessment and Auditing
Each domain is further divided into specific objectives. For example, the Security Monitoring and Analysis domain includes objectives on topics such as log analysis, intrusion detection, and security information and event management (SIEM).
To prepare for the CySA+ exam, it is important to have a strong understanding of all six domains. You can use a variety of resources to prepare, including CompTIA study guide, online courses, and practice exams. By understanding the exam objectives and using effective study materials, you can increase your chances of passing the exam and earning your CySA+ certification.
The CySA+ certification is a valuable asset for cybersecurity professionals. It demonstrates your expertise in implementing and maintaining effective cybersecurity measures. By passing the CS0-003 exam, you will validate your skills and knowledge and gain a competitive edge in the industry.
Domain 1: Threat Detection and Analysis
This domain covers the knowledge and skills required to detect and analyze threats to an organization's cybersecurity infrastructure.
Specific objectives include:
- Identifying and analyzing security events and incidents
- Using security monitoring tools and techniques
- Investigating and analyzing security breaches
- Identifying and analyzing malware
- Understanding and analyzing threat intelligence
To prepare for this domain, you should have a strong understanding of security monitoring tools and techniques, as well as experience in investigating and analysing security breaches. You should also be familiar with different types of malware and threat intelligence sources.
By understanding the objectives of this domain and using effective study materials, you can increase your chances of passing the CySA+ exam and earning your certification.
Domain 2: Vulnerability Management
This domain covers the knowledge and skills required to manage vulnerabilities in an organisation's cybersecurity infrastructure.
Specific objectives include:
- Identifying and assessing vulnerabilities
- Prioritising and remediating vulnerabilities
- Patching and updating software
- Conducting vulnerability scans
- Understanding and using vulnerability management tools
To prepare for this domain, you should have a strong understanding of vulnerability management best practices, as well as experience in using vulnerability scanning tools. You should also be familiar with different types of vulnerabilities and how to prioritize and remediate them.
By understanding the objectives of this domain and using effective study materials, you can increase your chances of passing the CySA+ exam and earning your certification.
Domain 3: Incident Response
This domain covers the knowledge and skills required to respond to cybersecurity incidents.
Specific objectives include:
- Developing and implementing incident response plans
- Responding to and managing security incidents
- Documenting and reporting security incidents
- Working with law enforcement and other external stakeholders
- Understanding and using incident response tools
To prepare for this domain, you should have a strong understanding of incident response best practices, as well as experience in developing and implementing incident response plans. You should also be familiar with different types of security incidents and how to respond to them.
By understanding the objectives of this domain and using effective study materials, you can increase your chances of passing the CySA+ exam and earning your certification.
Domain 4: Security Operations and Monitoring
This domain covers the knowledge and skills required to operate and monitor a cybersecurity infrastructure.
Specific objectives include:
- Monitoring and analyzing security events
- Managing and responding to security alerts
- Maintaining security logs and records
- Using security information and event management (SIEM) tools
- Understanding and using security operations best practices
To prepare for this domain, you should have a strong understanding of security operations best practices, as well as experience in using SIEM tools. You should also be familiar with different types of security events and how to respond to them.
By understanding the objectives of this domain and using effective study materials, you can increase your chances of passing the CySA+ exam and earning your certification.
Domain 5: Reporting and Communication
This domain covers the knowledge and skills required to communicate cybersecurity risks and incidents to management and other stakeholders.
Specific objectives include:
- Writing and delivering effective security reports
- Communicating with management and other stakeholders about cybersecurity risks
- Working with the media and other external stakeholders
- Understanding and using communication best practices
To prepare for this domain, you should have a strong understanding of communication best practices, as well as experience in writing and delivering security reports. You should also be familiar with different types of cybersecurity risks and how to communicate them effectively.
By understanding the objectives of this domain and using effective study materials, you can increase your chances of passing the CySA+ exam and earning your certification.
How to Choose Reliable CS0-003 Dumps
Choosing reliable CompTIA CySA+ (CS0-003) exam dumps can be a challenge.
Here are a few tips to help you make the best decision:
Check the source: Make sure the dumps you are considering come from a reputable source. There are many websites that sell dumps, but not all of them are created equal. Do some research to find a source that has a good reputation for providing accurate and up-to-date dumps.
Read reviews: Once you have found a few potential sources, read reviews from other users. This can give you a good idea of the quality of the dumps and the level of support you can expect from the seller.
Check the format: Make sure the dumps are in a format that you are comfortable with. Some dumps are provided in PDF format, while others are provided in a more interactive format, such as a practice exam simulator.
Consider the price: The price of dumps can vary significantly. Don't be afraid to shop around to find the best deal. However, keep in mind that the cheapest dumps are not always the best.
By following these tips, you can increase your chances of finding reliable CS0-003 exam dumps that will help you prepare for and pass the exam.
Study Plan for CySA+ CS0-003
To prepare for the CompTIA CySA+ (CS0-003) exam, it is important to develop a study plan that covers all of the exam objectives.
Here is a suggested study plan:
- Start by reviewing the exam objectives. This will give you a good overview of the topics that will be covered on the exam.
- Next, gather your study materials. This may include textbooks, online courses, and practice exams.
- Create a study schedule. Breaking down your studying into smaller chunks will make it more manageable.
- Start studying! Be sure to focus on the areas that you are weakest in.
- Take practice exams. This will help you to identify your strengths and weaknesses and to get a feel for the format of the exam.
- Review your notes. In the days leading up to the exam, take some time to review your notes and to go over any areas that you are still struggling with.
By following these steps, you can increase your chances of passing the CySA+ exam and earning your certification.
Key Topics Covered in CySA+ CS0-003 Dumps
CompTIA CySA+ (CS0-003) exam dumps cover a wide range of cybersecurity topics, including:
- Security monitoring and analysis
- Incident response
- Threat intelligence
- Vulnerability management
- Identity and access management
- Security assessment and auditing
Specific topics covered in the dumps include:
- Identifying and analyzing security events and incidents
- Using security monitoring tools and techniques
- Investigating and analyzing security breaches
- Identifying and analyzing malware
- Understanding and analyzing threat intelligence
- Developing and implementing incident response plans
- Responding to and managing security incidents
- Documenting and reporting security incidents
- Working with law enforcement and other external stakeholders
- Understanding and using incident response tools
- Identifying and assessing vulnerabilities
- Prioritising and remediating vulnerabilities
- Patching and updating software
- Conducting vulnerability scans
- Understanding and using vulnerability management tools
By using cs0-003 dumps, you can increase your chances of passing the CySA+ exam and earning your certification.
Hands-On Practice for CySA+ Dumps
In addition to studying the theory behind cybersecurity concepts, it is also important to get hands-on practice with the tools and techniques that you will be using on the job. Here are a few ways to get hands-on practice for the CySA+ exam:
Use a practice exam simulator. This is a software program that allows you to take practice exams in a realistic environment. Practice exam simulators can be found online or purchased from CompTIA.
Set up a home lab. This is a great way to get hands-on experience with cybersecurity tools and techniques. You can set up a home lab using virtual machines or physical hardware.
Volunteer your services. Many organizations are looking for volunteers to help with cybersecurity tasks. This is a great way to get hands-on experience and to give back to your community.
Take online courses. There are many online courses available that can teach you about cybersecurity concepts and tools. Some of these courses even offer hands-on labs.
By getting hands-on practice, you can increase your confidence and your chances of passing the CySA+ exam.
Common Challenges with CS0-003 Preparation
Preparing for the CompTIA CySA+ (CS0-003) exam can be challenging. Here are a few common challenges that you may face:
The exam is difficult. The CySA+ exam is a challenging exam that covers a wide range of cybersecurity topics. You will need to have a strong understanding of cybersecurity concepts and tools in order to pass the exam.
The exam is timed. You will have 165 minutes to complete the exam. This means that you will need to be able to manage your time wisely and to answer questions quickly and accurately.
The exam is expensive. The CySA+ exam costs $370. This can be a significant investment, so you will want to make sure that you are prepared before you take the exam.
The exam is constantly changing. CompTIA updates the CySA+ exam regularly to keep up with the latest cybersecurity trends. This means that you will need to stay up-to-date on the latest cybersecurity news and developments.
Despite these challenges, it is possible to pass the CySA+ exam with the right preparation. By using cs0-003 dumps, studying effectively, and getting hands-on practice, you can increase your chances of success.
Tips for Using CS0-003 Dumps Effectively
Here are a few tips for using CompTIA CySA+ (CS0-003) exam dumps effectively:
Use dumps from a reputable source. There are many websites that sell dumps, but not all of them are created equal. Do some research to find a source that has a good reputation for providing accurate and up-to-date dumps.
Make sure the dumps are in a format that you are comfortable with. Some dumps are provided in PDF format, while others are provided in a more interactive format, such as a practice exam simulator.
- Start by reviewing the exam objectives. This will give you a good overview of the topics that will be covered on the exam.
- Go through the dumps and identify the areas that you are weakest in. Focus on studying these areas.
- Take practice exams. This will help you to identify your strengths and weaknesses and to get a feel for the format of the exam.
- Review your notes. In the days leading up to the exam, take some time to review your notes and go over any areas that you are still struggling with.
By following these tips, you can increase your chances of passing the CySA+ exam and earning your certification.
Importance of CompTIA Certification in Cybersecurity
The CompTIA Certification is a valuable asset for cybersecurity professionals. It demonstrates your skills and knowledge in cybersecurity analysis and defense.
Earning the CySA+ certification can help you to:
- Advance your career. The CompTIA certification is a highly respected credential in the cybersecurity industry. Earning the certification can help you to qualify for promotions and new job opportunities.
- Increase your salary. Cybersecurity professionals with the CompTIA certification earn higher salaries than those without the certification.
- Stay up-to-date on the latest cybersecurity trends. The CompTIA certification is updated regularly to keep up with the latest cybersecurity threats and trends. This ensures that you have the skills and knowledge to protect your organization from the latest threats.
Gain a competitive edge. In today's competitive job market, earning the CompTIA certification can give you a competitive edge over other candidates.
If you are serious about a career in cybersecurity, earning the CompTIA certification is a smart investment. By using CS0-003 dumps and studying effectively, you can increase your chances of passing the exam and earning your certification.
Exam Retake Policy and Strategy DumpsBoss
The CompTIA CySA+ (CS0-003) exam retake policy is as follows:
- You can retake the exam as many times as you need to pass.
- There is a waiting period of 14 days between each attempt.
- You will need to pay the full exam fee each time you retake the exam.
If you fail the CySA+ exam, it is important to take some time to review your notes and to identify the areas that you need to improve on. You can also use cs0-003 dumps to help you prepare for your retake.
Here are a few tips for retaking the CySA+ exam:
- Review the exam objectives. This will help you to identify the areas that you need to focus on.
- Go through the dumps and identify the areas that you are weakest in. Focus on studying these areas.
- Take practice exams. This will help you to identify your strengths and weaknesses and to get a feel for the format of the exam.
- Review your notes. In the days leading up to the exam, take some time to review your notes and go over any areas that you are still struggling with.
By following these tips, you can increase your chances of passing the CySA+ exam on your retake.
Cost of the CySA+ CS0-003 Exam Dumps
The cost of CompTIA CySA+ (CS0-003) exam dumps varies depending on the source. However, you can expect to pay between $50 and $200 for a set of dumps.
When choosing a source for your dumps, it is important to consider the following factors:
- Reputation: Make sure that the source has a good reputation for providing accurate and up-to-date dumps.
- Format: Make sure that the dumps are in a format that you are comfortable with.
- Price: Compare the prices of dumps from different sources before making a decision.
Once you have chosen a source for your dumps, you can purchase them online or through a physical store.
In addition to the cost of the dumps, you will also need to pay the exam fee. The exam fee is $370.
The total cost of the CySA+ certification is therefore between $420 and $570.
Ensuring alignment with the latest CS0-003 objectives
To ensure that your preparation is aligned with the latest CS0-003 objectives, you should use up-to-date study materials.
Here are a few tips:
- Check the DumpsBoss website. DumpsBoss regularly updates the exam objectives on its website. Make sure that you are using study materials that are based on the latest objectives.
- Use dumps from a reputable source. Reputable sources will keep their dumps up-to-date with the latest exam objectives.
- Take practice exams. Practice exams can help you to identify areas where you need to improve your knowledge. Make sure that you are using practice exams that are based on the latest exam objectives.
By following these tips, you can ensure that your preparation is aligned with the latest CS0-003 objectives and that you are well-prepared for the exam.
Post-Certification Opportunities
Earning the CompTIA CySA+ (CS0-003) certification opens up a world of opportunities for your cybersecurity career. Here are a few of the most common post-certification opportunities:
Security Analyst: Security analysts are responsible for monitoring and analysing security events, identifying and responding to threats, and developing and implementing security policies and procedures.
Incident Responder: Incident responders are responsible for responding to and managing security incidents. This includes investigating the incident, containing the damage, and restoring normal operations.
Threat Intelligence Analyst: Threat intelligence analysts are responsible for collecting, analysing, and disseminating information about threats to an organisation security. This information can be used to develop and implement security measures to protect the organisation from these threats.
Cybersecurity Consultant: Cybersecurity consultants provide advice and guidance to organizations on how to improve their cybersecurity posture. This can include conducting security assessments, developing security plans, and implementing security measures.
Earning the CySA+ certification can also help you to advance your career in other areas of cybersecurity, such as security management, risk management, and compliance.
Final Tips
Here are a few final tips to help you prepare for and pass the CompTIA CySA+ (CS0-003) exam:
Start studying early. Don't wait until the last minute to start studying. Give yourself plenty of time to review the material and to take practice exams.
Use a variety of study materials. Don't rely on just one source of information. Use a variety of study materials, such as textbooks, online courses, and practice exams, to get a well-rounded understanding of the material.
Take practice exams. Practice exams are one of the best ways to prepare for the actual exam. Take as many practice exams as you can to identify your strengths and weaknesses and to get a feel for the format of the exam.
Get enough sleep. Don't try to cram all of your studying into the night before the exam. Get a good night's sleep before the exam so that you are well-rested and ready to perform your best.
Stay positive. Believe in yourself and your ability to pass the exam. A positive attitude will go a long way in helping you to achieve your goals.
Good luck with your exam!
Fast Free Updates for 90 days to Cover Latest Questions “CS0-003 Dumps” Order Now!
Sample Multiple Choice Questions for CompTIA CS0-003 Exam Dumps
QUESTION NO: 1
Which of the following tools would work best to prevent the exposure of PII outside of an organization?
A. PAM
B. IDS
C. PKI
D. DLP
Explanation:
Data loss prevention (DLP) is a tool that can prevent the exposure of PII outside of an organization by monitoring, detecting, and blocking sensitive data in motion, in use, or at rest.
QUESTION NO: 2
An incident response team is working with law enforcement to investigate an active web server compromise. The decision has been made to keep the server running and to implement compensating controls for a period of time. The web service must be accessible from the internet via the reverse proxy and must connect to a database server. Which of the following compensating controls will help contain the adversary while meeting the other requirements? (Select two).
A. Drop the tables on the database server to prevent data exfiltration.
B. Deploy EDR on the web server and the database server to reduce the adversaries capabilities.
C. Stop the httpd service on the web server so that the adversary can not use web exploits
D. use micro segmentation to restrict connectivity to/from the web and database servers.
E. Comment out the HTTP account in the / etc/passwd file of the web server
F. Move the database from the database server to the web server.
Explanation:
Deploying EDR on the web server and the database server to reduce the adversaries capabilities and using micro segmentation to restrict connectivity to/from the web and database servers are two compensating controls that will help contain the adversary while meeting the other requirements. A compensating control is a security measure that is implemented to mitigate the risk of a vulnerability or an attack when the primary control is not feasible or effective. EDR
stands for Endpoint Detection and Response, which is a tool that monitors endpoints for malicious activity and provides automated or manual response capabilities. EDR can help contain the adversary by detecting and blocking their actions, such as data exfiltration, lateral movement, privilege escalation, or command execution. Micro segmentation is a technique that divides a network into smaller segments based on policies and rules, and applies granular access controls to each segment. Micro segmentation can help contain the adversary by isolating the web and database servers from other parts of the network, and limiting the traffic that can flow between them. Official
References:
https://partners.comptia.org/docs/default-source/resources/comptia-cysa-cs0-002-exam-objectives
https://www.comptia.org/certifications/cybersecurity-analyst
https://www.comptia.org/blog/the-new-comptia-cybersecurity-analyst-your-questions-answered
QUESTION NO: 3
Which of the following best describes the document that defines the expectation to network customers that patching will only occur between 2:00 a.m. and 4:00 a.m.?
A. SLA
B. LOI
C. MOU
D. KPI
Explanation:
SLA (Service Level Agreement) is the best term to describe the document that defines the expectation to network customers that patching will only occur between 2:00 a.m. and 4:00 a.m., as it reflects the agreement between a service provider and a customer that specifies the services, quality, availability, and responsibilities that are agreed upon. An SLA is a common type of document that is used in various industries and contexts, such as IT, telecom, cloud computing, or outsourcing. An SLA typically includes metrics and indicators to measure the performance and quality of the service, such as uptime, response time, or resolution time. An SLA also defines the consequences or remedies for any breaches or failures of the service, such as penalties, refunds, or credits. An SLA can help to manage customer expectations, formalize communication, improve productivity, and strengthen relationships. The other terms are not as accurate as SLA, as they describe different types of documents or concepts. LOI (Letter of Intent) is a document that outlines the main terms and conditions of a proposed agreement between two or more parties, before a formal contract is signed. An LOI is usually non-binding and expresses the intention or interest of the parties to enter into a future agreement. An LOI can help to clarify the key points of a deal, facilitate negotiations, or demonstrate commitment. MOU (Memorandum of Understanding) is a document that describes a mutual agreement or cooperation between two or more parties, without creating any legal obligations or commitments. An MOU is usually more formal than an LOI, but less formal than a contract. An MOU can help to establish a common ground, define roles and responsibilities, or outline expectations and goals. KPI (Key Performance Indicator) is a concept that refers to a measurable value that demonstrates how effectively an organization or individual is achieving its key objectives or goals. A KPI is usually quantifiable and specific, such as revenue growth, customer satisfaction, or employee retention. A KPI can help to track progress, evaluate performance, or identify areas for improvement.
QUESTION NO: 4
A vulnerability management team is unable to patch all vulnerabilities found during their weekly scans. Using the third-party scoring system described below, the team patches the most urgent vulnerabilities:
Additionally, the vulnerability management team feels that the metrics Smear and Channing are less important than the others, so these will be lower in priority. Which of the following vulnerabilities should be patched first, given the above third-party scoring system?
A. InLoud:
Cobain: Yes
Grohl: No Novo: Yes Smear: Yes Channing: No
B. TSpirit:
Cobain: Yes Grohl: Yes Novo: Yes Smear: No Channing: No
C. ENameless: Cobain: Yes Grohl: No Novo: Yes Smear: No Channing: No
D. PBleach: Cobain: Yes Grohl: No Novo: No Smear: No Channing: Yes
Explanation:
The vulnerability that should be patched first, given the above third-party scoring system, is: TSpirit: Cobain: Yes Grohl: Yes Novo: Yes Smear: No Channing: No
This vulnerability has three out of five metrics marked as Yes, which indicates a high severity level. The metrics Cobain, Grohl, and Novo are more important than Smear and Channing, according to the vulnerability management team. Therefore, this vulnerability poses a greater risk than the other vulnerabilities and should be patched first.
QUESTION NO: 5
A security audit for unsecured network services was conducted, and the following output was generated: Which of the following services should the security team investigate further? (Select two).
A. 21
B. 22
C. 23
D. 636
E. 1723
F. 3389
Explanation:
The output shows the results of a port scan, which is a technique used to identify open ports and services running on a network host. Port scanning can be used by attackers to discover potential vulnerabilities and exploit them, or by defenders to assess the security posture and configuration of their network devices1
The output lists six ports that are open on the target host, along with the service name and version associated with each port. The service name indicates the type of application or protocol that is using the port, while the version indicates the specific release or update of the service. The service name and version can provide useful information for both attackers and defenders, as they can reveal the capabilities, features, and weaknesses of the service.
Among the six ports listed, two are particularly risky and should be investigated further by the security team: port 23 and port 636.
Port 23 is used by Telnet, which is an old and insecure protocol for remote login and command execution. Telnet does not encrypt any data transmitted over the network, including usernames and passwords, which makes it vulnerable to eavesdropping, interception, and modification by attackers. Telnet also has many known vulnerabilities that can allow attackers to gain unauthorized access, execute arbitrary commands, or cause denial-of-service attacks on the target host23

Port 636 is used by LDAP over SSL/TLS (LDAPS), which is a protocol for accessing and modifying directory services over a secure connection. LDAPS encrypts the data exchanged between the client and the server using SSL/TLS certificates, which provide authentication, confidentiality, and integrity. However, LDAPS can also be vulnerable to attacks if the certificates are not properly configured, verified, or updated. For example, attackers can use self-signed or expired certificates to perform man-in-the-middle attacks, spoofing attacks, or certificate revocation attacks on LDAPS connections.
Therefore, the security team should investigate further why port 23 and port 636 are open on the target host, and what services are running on them. The security team should also consider disabling or replacing these services with more secure alternatives, such as SSH for port 23 and StartTLS for port 6362
QUESTION NO: 6
A security analyst at a company called ACME Commercial notices there is outbound traffic to a host IP that resolves to https://offce365password.acme.co. The site's standard VPN logon page is www.acme.com/logon. Which of the following is most likely true?
A. This is a normal password change URL.
B. The security operations center is performing a routine password audit.
C. A new VPN gateway has been deployed
D. A social engineering attack is underway
Explanation:
A social engineering attack is underway is the most likely explanation for the outbound traffic to a host IP that resolves to https://offce365password.acme.co, while the site’s standard VPN logon page is www.acme.com/logon. A social engineering attack is a technique that exploits human psychology and behavior to manipulate people into performing actions or divulging information that benefit the attackers. A common type of social engineering attack is phishing, which involves sending fraudulent emails or other messages that appear to come from a legitimate source, such as a company or a colleague, and lure the recipients into clicking on malicious links or attachments, or entering their credentials or other sensitive information on fake websites. In this case, the attackers may have registered a domain name that looks similar to the company’s domain name, but with a typo (offce365 instead of office365), and set up a fake website that mimics the company’s VPN logon page. The attackers may have also sent phishing emails to the company’s employees, asking them to reset their passwords or log in to their VPN accounts using the malicious link. The security analyst should investigate the source and content of the phishing emails, and alert the employees not to click on any suspicious links or enter their credentials on any untrusted websites. Official
References:
https://partners.comptia.org/docs/default-source/resources/comptia-cysa-cs0-002-exam-objectives
https://www.comptia.org/certifications/cybersecurity-analyst
https://www.comptia.org/blog/the-new-comptia-cybersecurity-analyst-your-questions-answered
QUESTION NO: 7
Which of the following items should be included in a vulnerability scan report? (Choose two.)
A. Lessons learned
B. Service-level agreement
C. Playbook
D. Affected hosts
E. Risk score
F. Education plan
Explanation:
A vulnerability scan report should include information about the affected hosts, such as their IP addresses, hostnames, operating systems, and services. It should also include a risk score for each vulnerability, which indicates the severity and potential impact of the vulnerability on the host and the organization. Official
References: https://www.first.org/cvss/
QUESTION NO: 8
An analyst is reviewing a vulnerability report for a server environment with the following entries: Which of the following systems should be prioritized for patching first?
A. 10.101.27.98
B. 54.73.225.17
C. 54.74.110.26
D. 54.74.110.228
Explanation:
The system that should be prioritized for patching first is 54.74.110.228, as it has the highest number and severity of vulnerabilities among the four systems listed in the vulnerability report. According to the report, this system has 12 vulnerabilities, with 8 critical, 3 high, and 1 medium severity ratings. The critical vulnerabilities include CVE-2019-0708 (BlueKeep), CVE-2019-1182 (DejaBlue), CVE-2017-0144 (EternalBlue), and CVE-2017-0145 (EternalRomance), which are all remote code execution vulnerabilities that can allow an attacker to compromise the system without any user interaction or authentication. These vulnerabilities pose a high risk to the system and should be patched as soon as possible.
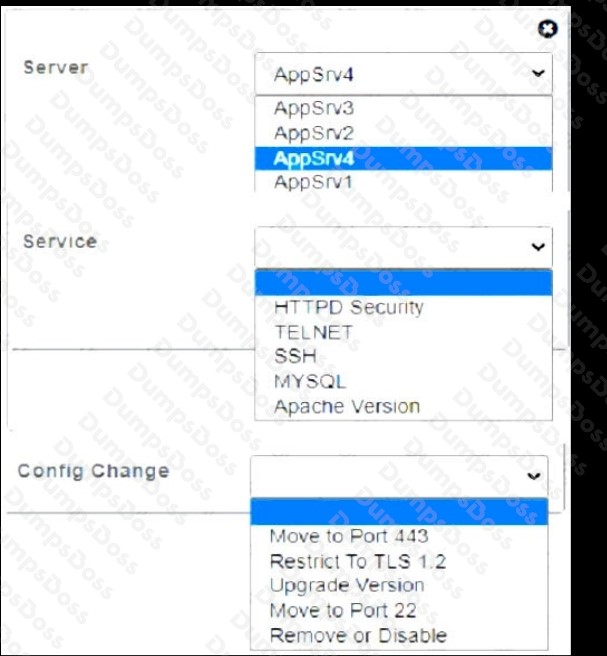
QUESTION NO: 9 - (SIMULATION)
You are a cybersecurity analyst tasked with interpreting scan data from Company As servers You must verify the requirements are being met for all of the servers and recommend changes if you find they are not
The company's hardening guidelines indicate the following
• TLS 1 2 is the only version of TLS running.
• Apache 2.4.18 or greater should be used.
• Only default ports should be used.
INSTRUCTIONS
using the supplied data. record the status of compliance With the company’s guidelines for each server.
The question contains two parts: make sure you complete Part 1 and Part 2. Make recommendations for Issues based ONLY on the hardening guidelines provided.
Part 1: AppServ1:
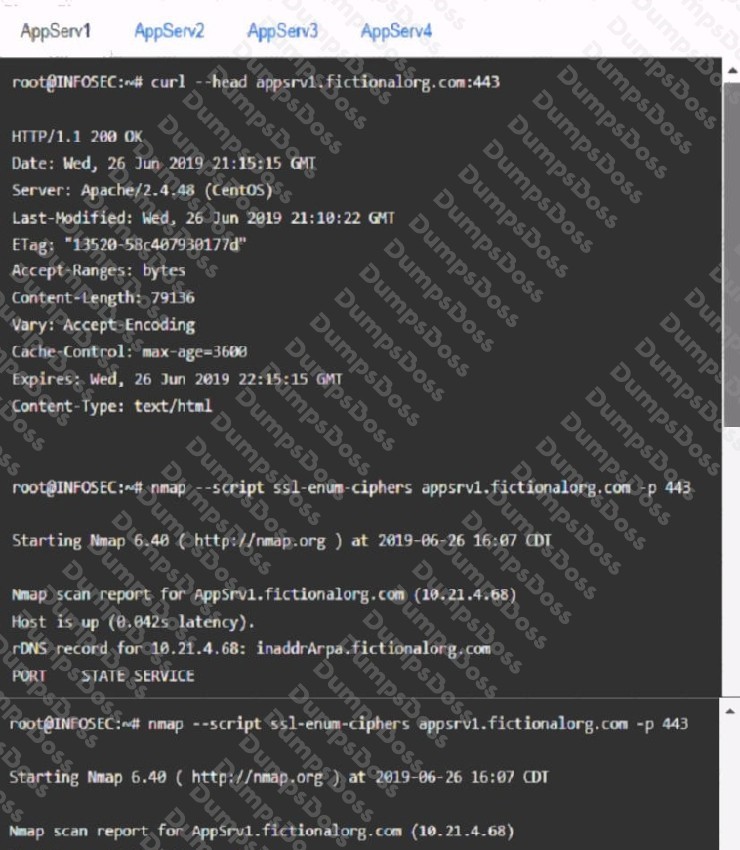
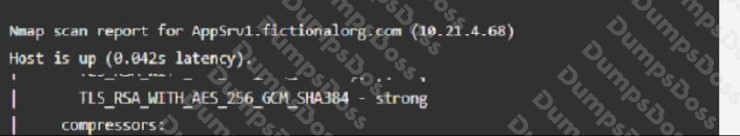
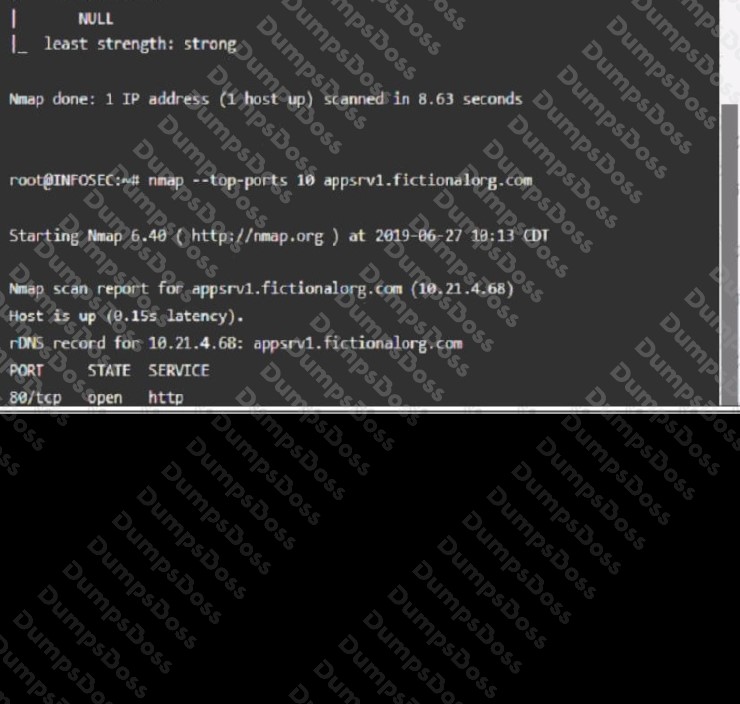
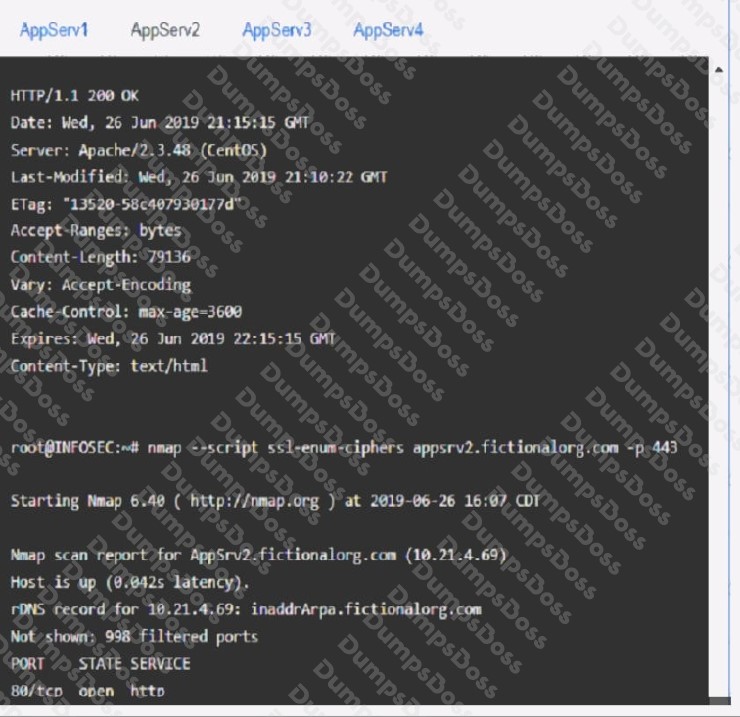
AppServ2:
AppServ3:
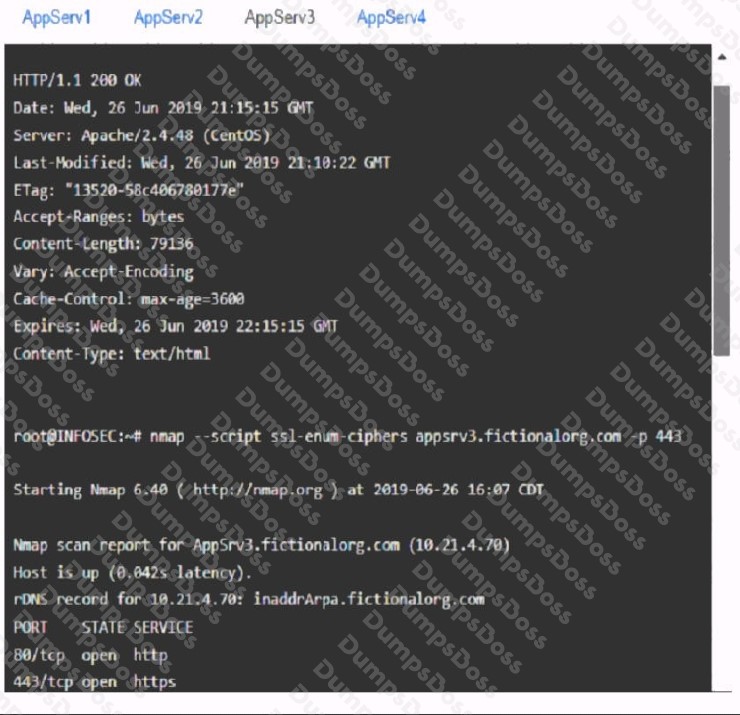
AppServ4:
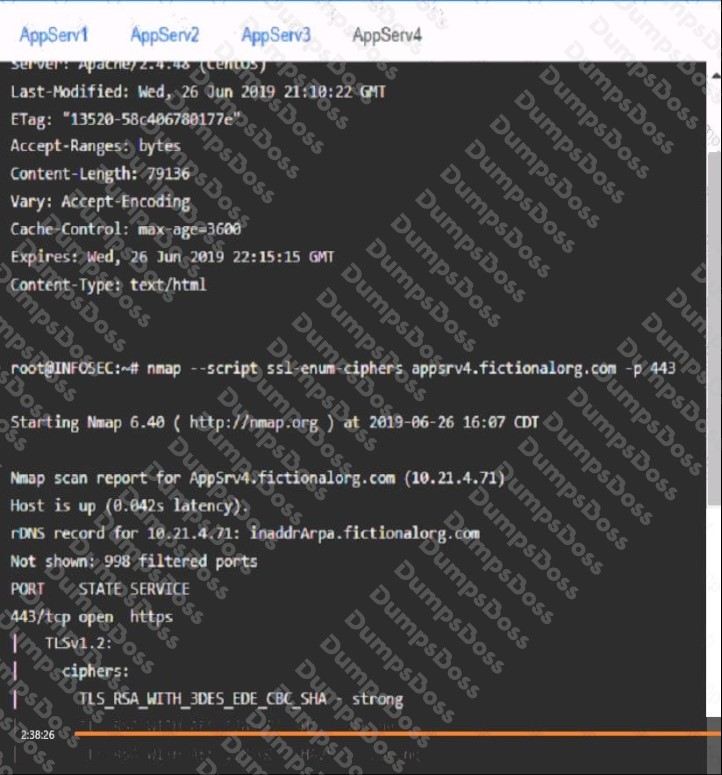
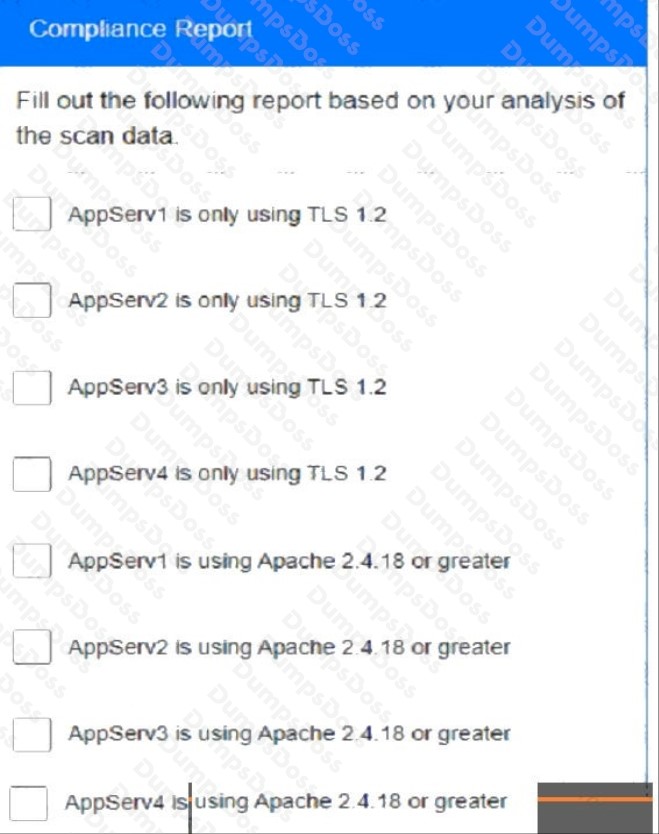
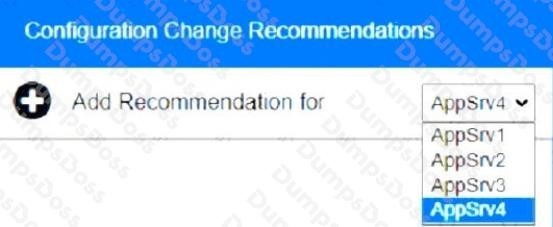
Part 2:
QUESTION NO: 10
An incident response analyst notices multiple emails traversing the network that target only the administrators of the company. The email contains a concealed URL that leads to an unknown website in another country.
Which of the following best describes what is happening? (Choose two.)
A. Beaconinq
B. Domain Name System hijacking
C. Social engineering attack
D. On-path attack
E. Obfuscated links
F. Address Resolution Protocol poisoning
Explanation:
A social engineering attack is a type of cyberattack that relies on manipulating human psychology rather than exploiting technical vulnerabilities. A social engineering attack may involve deceiving, persuading, or coercing users into performing actions that benefit the attacker, such as clicking on malicious links, divulging sensitive information, or granting access to restricted resources. An obfuscated link is a link that has been disguised or altered to hide its true destination or purpose. Obfuscated links are often used by attackers to trick users into visiting malicious websites or downloading malware. In this case, an incident response analyst notices multiple emails traversing the network that target only the administrators of the company. The email contains a concealed URL that leads to an unknown website in another country. This indicates that the analyst is witnessing a social engineering attack using obfuscated links.
FAQs About CompTIA CySA+ CS0-003 Exam Dumps
Q: What are CompTIA CySA+ CS0-003 exam dumps?
A: CompTIA CySA+ CS0-003 exam dumps are a collection of practice questions and answers that have been designed to help you prepare for the CompTIA CySA+ (CS0-003) exam.
Q: Are CompTIA CySA+ CS0-003 exam dumps reliable?
A: Yes, CompTIA CySA+ CS0-003 exam dumps are reliable because they are created by subject matter experts and are regularly updated to reflect the latest exam objectives.
Q: How can CompTIA CySA+ CS0-003 exam dumps help me prepare for the exam?
A: CompTIA CySA+ CS0-003 exam dumps can help you prepare for the exam by providing you with a comprehensive overview of the exam objectives, identifying your strengths and weaknesses, and helping you improve your time management skills.
Q: How much do CompTIA CySA+ CS0-003 exam dumps cost?
A: The cost of CompTIA CySA+ CS0-003 exam dumps varies depending on the vendor. However, you can expect to pay between $50 and $200 for a set of dumps.
Q: Where can I buy CompTIA CySA+ CS0-003 exam dumps?
A: You can purchase CompTIA CySA+ CS0-003 exam dumps from a variety of online and offline vendors.


