How this question relates to the CompTIA PenTest+ (PT0-002) Exam
This question aligns with the CompTIA PenTest+ (PT0-002) Exam outline under the domain of "Assessment and Analysis." Specifically, it tests the candidate's knowledge of "identifying and analyzing security vulnerabilities using vulnerability management tools." By demonstrating an understanding of the tool's capabilities and limitations, as well as the process of vulnerability assessment and risk management, candidates can showcase their proficiency in this critical area of penetration testing.
Definition of Hardening in Cybersecurity
Hardening in cybersecurity refers to the process of strengthening a system or network to reduce its vulnerability to cyberattacks. It involves implementing various security measures to make
it is more difficult for attackers to exploit weaknesses and gain unauthorized access. Hardening typically includes techniques such as:
- Applying security patches and updates
- Configuring firewalls and intrusion detection/prevention systems
- Disabling unnecessary services and ports
- Restricting user privileges and implementing strong password policies
- Encrypting sensitive data
By implementing these measures, organizations can significantly reduce the risk of successful cyberattacks and protect their critical assets.
Methods of Device Hardening
Device hardening is a cybersecurity process that reduces vulnerabilities and strengthens security by minimizing attack surfaces. It involves various techniques like patching, strong passwords, access control, encryption, and disabling unnecessary services. This makes devices more resistant to cyber threats.
Disabling Unnecessary Services and Features
Disabling unnecessary services and features is a critical security measure that can significantly reduce the attack surface of a system or network. By eliminating unneeded components, organizations can minimize the potential entry points for attackers and make it more difficult for them to exploit vulnerabilities.
Some common examples of unnecessary services and features that should be disabled include:
- Unused network ports
- Un necessary protocols and services (e.g., Telnet, FTP)
- Default accounts and services
- Unneeded software applications and features
By carefully reviewing the system configuration and identifying non-essential services and features, organizations can disable them to enhance their overall security posture. This practice is particularly important for systems that are exposed to the internet or handle sensitive data.
Applying Security Patches and Updates
Applying security patches and updates is a fundamental aspect of cybersecurity that helps organizations protect their systems and networks from known vulnerabilities. Software vendors regularly release patches and updates to address security flaws and vulnerabilities in their products. These updates often include fixes for critical vulnerabilities that could be exploited by attackers to gain unauthorized access, steal data, or disrupt operations.
Organizations should establish a robust patch management process to ensure that security patches and updates are applied promptly and effectively. This process should include:
- Regularly scanning systems for missing patches and updates
- Prioritizing and testing patches before deployment
- Deploying patches and updates in a timely manner
- Verifying that patches have been successfully applied
By implementing a proactive patch management process, organizations can significantly reduce the risk of successful cyberattacks and protect their critical assets.
Enforcing Strong Authentication Mechanisms
Enforcing strong authentication mechanisms is crucial for protecting systems and networks from unauthorized access. Traditional authentication methods, such as passwords, are no longer sufficient to safeguard against sophisticated cyberattacks. Organizations must implement multi-factor authentication (MFA) and other strong authentication mechanisms to enhance their security posture.
MFA requires users to provide multiple forms of identification, such as a password, a one-time code sent to their mobile phone, or a biometric factor (e.g., fingerprint or facial recognition). This makes it significantly more difficult for attackers to gain unauthorized access, even if they obtain a user's password.
Other strong authentication mechanisms include:
- Smart cards
- Security tokens
- Biometric authentication
By implementing strong authentication mechanisms, organizations can significantly reduce the risk of successful cyberattacks and protect their critical assets.
Configuring Firewalls and Network Security
Firewalls and network security devices are essential components of any cybersecurity strategy. They act as a barrier between internal networks and the outside world, monitoring and controlling incoming and outgoing traffic. Proper configuration of these devices is crucial to protect systems and networks from unauthorized access, malicious attacks, and data breaches.
When configuring firewalls and network security devices, organizations should consider the following best practices:
- Enable Stateful Inspection: Stateful inspection allows firewalls to track the state of network connections and make more informed decisions about allowing or blocking traffic.
- Use Strong Access Control Lists (ACLs): ACLs define the rules for allowing or denying traffic based on source and destination IP addresses, ports, and other criteria.
- Block Unnecessary Ports and Services: Firewalls should be configured to block all unnecessary ports and services to reduce the attack surface.
- Implement Intrusion Detection and Prevention Systems (IDS/IPS): IDS/IPS devices can detect and block malicious traffic and network attacks.
- Monitor and Audit Firewall Logs: Regularly monitoring and auditing firewall logs can help identify suspicious activity and potential security breaches.
By following these best practices, organizations can significantly enhance their network security posture and protect their critical assets from cyber threats.
Implementing Least Privilege Principles
The principle of least privilege states that users should be granted only the minimum level of access necessary to perform their job functions. This principle helps to reduce the risk of unauthorized access to sensitive data and systems in the event of a security breach.
To implement least privilege principles, organizations should:
- Review and audit user permissions regularly: Ensure that users have only the permissions they need to perform their job duties.
- Use role-based access control (RBAC): RBAC assigns permissions based on job roles, making it easier to manage and enforce least privilege.
- Implement mandatory access control (MAC): MAC enforces access controls based on labels assigned to data and users, ensuring that users can only access data that they are authorized to.
- Use privilege escalation mechanisms: Implement mechanisms that allow users to temporarily elevate their privileges when necessary, but only for specific tasks.
- Monitor and audit user activity: Regularly monitor user activity to identify any suspicious or unauthorized access attempts.
By implementing least privilege principles, organizations can significantly reduce the risk of data breaches and unauthorized access to critical systems.
Monitoring and Logging Activities
Monitoring and logging activities are crucial for maintaining the security of systems and networks. By tracking and recording events and activities, organizations can detect suspicious behavior, identify security incidents, and respond promptly to threats.
Effective monitoring and logging practices involve:
- Identifying critical systems and data: Determine which systems and data are most critical to the organization and require the highest level of monitoring.
- Selecting appropriate logging tools: Choose logging tools that can capture the necessary data and provide the desired level of detail.
- Configuring logs: Configure logs to capture relevant events and activities, such as user logins, file access, and system changes.
- Regularly reviewing logs: Establish a process for regularly reviewing logs to identify any suspicious or unauthorized activities.
- Storing logs securely: Ensure that logs are stored securely to prevent unauthorized access and tampering.
By implementing robust monitoring and logging practices, organizations can gain visibility into their systems and networks, enabling them to detect and respond to security threats effectively.
How this topic is tested in the CompTIA PT0-002 Exam
The CompTIA PenTest+ (PT0-002) Exam covers a wide range of topics related to penetration testing, including monitoring and logging activities. Candidates are expected to demonstrate their knowledge of:
- The importance of monitoring and logging for security
- Different types of logging tools and their capabilities
- How to configure logs to capture relevant events
- Techniques for analyzing and interpreting logs
- Best practices for storing logs securely
Candidates may be presented with scenarios or questions that require them to apply their knowledge of monitoring and logging to real-world situations. For example, they may be asked to identify potential security risks based on log data or to recommend improvements to an organization's logging practices.
By demonstrating a strong understanding of monitoring and logging activities, candidates can increase their chances of success on the CompTIA PT0-002 Exam.
Conclusion
Implementing strong security measures is essential for protecting systems and networks from cyber threats. By following best practices such as applying security patches, configuring firewalls, and monitoring activities, organizations can significantly reduce their risk of successful cyberattacks.
The CompTIA PenTest+ (PT0-002) Exam tests candidates' knowledge of a wide range of penetration testing topics, including security assessment, vulnerability management, and reporting. By understanding the concepts covered in this outline, candidates can prepare effectively for the exam and demonstrate their proficiency in penetration testing.
Remember, cybersecurity is an ongoing process that requires continuous monitoring, assessment, and improvement. By staying up-to-date with the latest threats and best practices, organizations can protect their critical assets and maintain a strong security posture.
We hope this outline has provided you with a comprehensive overview of the topics covered in the CompTIA PenTest+ (PT0-002) Exam. If you have any further questions, please do not hesitate to contact us.
Special Discount: Offer Valid For Limited Time “PT0-002 Exam” Order Now!
Sample Questions for CompTIA PT0-002 Dumps
Actual exam question from CompTIA PT0-002 Exam.
An Nmap scan of a network switch reveals the following:
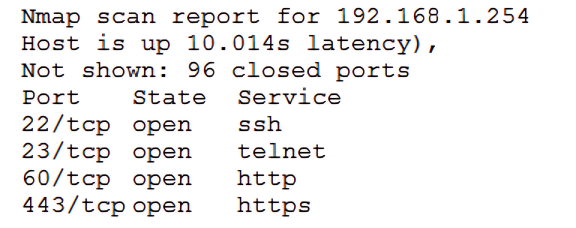
Which of the following technical controls will most likely be the FIRST recommendation for this device?
A. Encrypted passwords
B. System-hardening techniques
C. Multifactor authentication
D. Network segmentation


